Windows stores user credentials in the Security Accounts Manager (SAM) database located at C:\Windows\System32\config\SAM, which is locked while Windows is running. Passwords are stored as hashes using algorithms like NTLM or NTLMv2.
Modern Windows systems add extra protection using the Data Protection API (DPAPI). For domain-joined computers, passwords may also be stored in the Active Directory database on domain controllers.
Windows Authentication Process
-
Initial Login Process:
- WinLogon.exe (uses
Secur32.dll) interacts with LogonUI, which connects to the Credential Provider. - LogonUI returns credentials to WinLogon.exe.
- WinLogon.exe calls lsass.exe which uses
Lsasrv.dll.
- WinLogon.exe (uses
-
Authentication Paths:
-
For Local/Non-Domain Joined systems:
- Authentication Packages process credentials.
- NTLM (using
Msv1_0.dll) authenticates against SAM. - SAM (using
Samsrv.dll) retrieves account information from the Registry.
-
For Remote/Domain Joined systems:
- Authentication Packages process credentials.
- NTLM (using
Msv1_0.dll) or Kerberos (usingKerberos.dll) protocols are used. - Netlogon (using
Netlogon.dll) communicates with AD Directory Services (usingNtdsa.dll).
-
-
Post-Authentication:
- WinLogon.exe calls CreateDesktop().
- User profile is loaded.
- Registry settings are applied.
- userinit.exe launches explorer.exe.
LSASS
The
Link to originalLocal Security Authority Subsystem Service(LSASS) is a process in Windows that is responsible for enforcing the security policy on the system.
Thelsass.exefile used by Windows is located in the%SystemRoot%\System32\Lsass.exe.
SAM
The
Link to originalSecurity Account Manager(SAM) is a Windows database file that stores user passwords for authenticating local and remote users. It’s located at%SystemRoot%/system32/config/SAMand mounted on HKLM/SAM. Viewing it requires SYSTEM level permissions.
NTDS
Domain-joined Windows systems send logon requests to
Link to originalDomain Controllers(DC) in the same Active Directory forest. Each Domain Controller hosts anNTDS.ditfile, which is synchronized across all DCs except Read-Only Domain Controllers. It’s typically stored at%SystemRoot%\ntds.dit.
Credential Manager
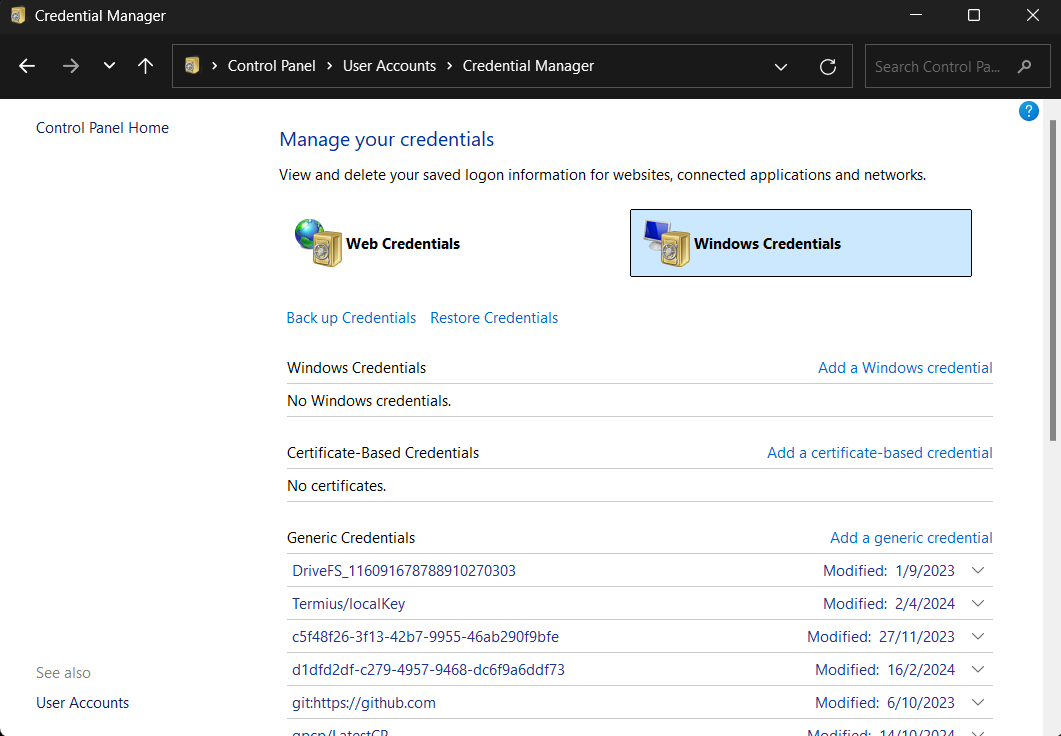
Credential Manager is a built-in Windows feature that allows users to save both Windows and Web credentials. These saved credentials are stored in each user’s Credential Locker, organized by user profile.
The credentials are encrypted and stored at:
C:\Users\[Username]\AppData\Local\Microsoft\[Vault/Credentials]\LaZagne
The LaZagne project is an open source application used to retrieve lots of passwords stored on a local computer.
# Retrieve all the passwords
LaZagne.exe all
# OR - Find "password" string in files - CMD
findstr /SIM /C:"password" *.txt *.ini *.cfg *.config *.xml *.git *.ps1 *.yml