Metasploit Framework is an open source platform that supports vulnerability research, exploit development, and the creation of custom security tools.
Base Files
By default, all base files related to the Metasploit Framework are located in /usr/share/metasploit-framework on most security-focused distributions (e.g., Kali, ParrotOS).
These files are organized into different parts that enable msfconsole to function properly.
Modules
The modules directory contains all the modules supported in msfconsole.
Default location:/usr/share/metasploit-framework/modules/
Plugins
The plugins directory contains all available plugins, providing additional flexibility in msfconsole by allowing manual or automatic loading.
Default location:/usr/share/metasploit-framework/plugins/
Scripts
The scripts directory contains Meterpreter functionality and other useful scripts.
Default location:/usr/share/metasploit-framework/scripts/
Tools
The tools directory contains command-line utilities that can be executed directly from the msfconsole menu.
Default location:/usr/share/metasploit-framework/tools/
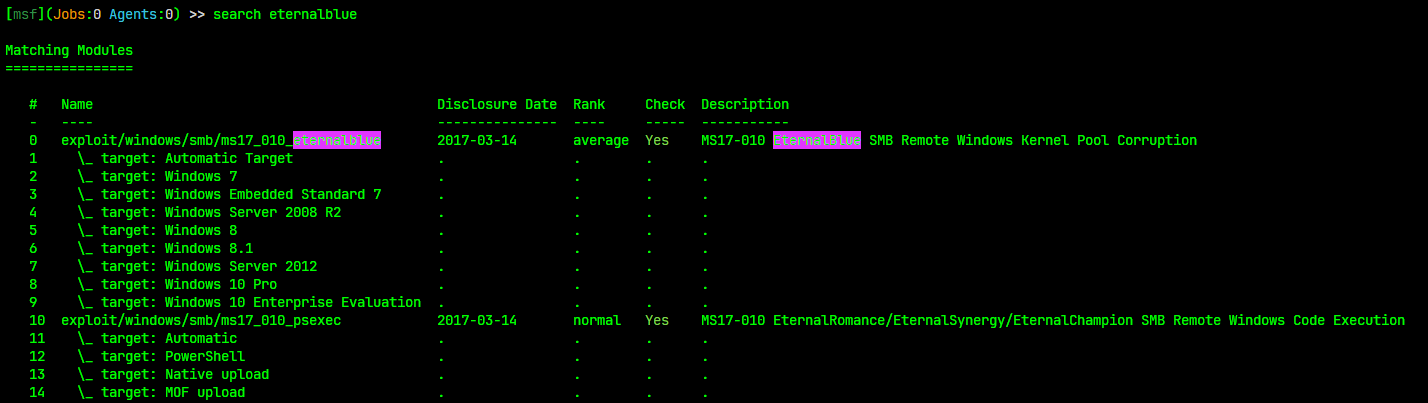
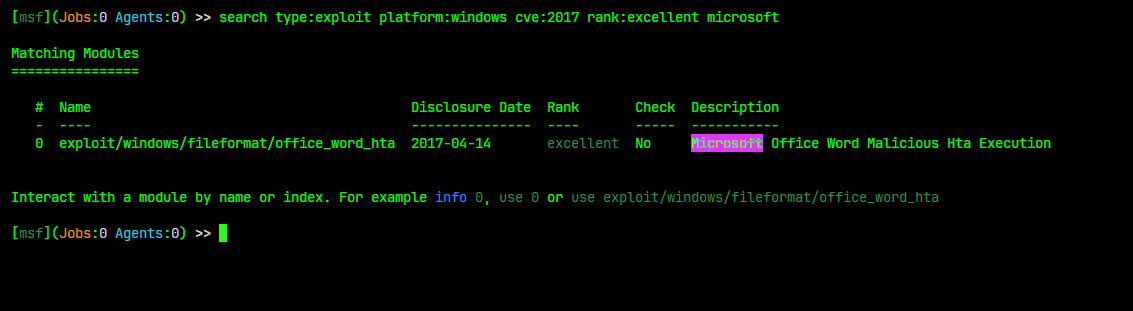
Searching For Modules
The Msfconsole offers a powerful search functionality. If you’re looking for a specific module, you can use specific tags to find the most suitable one for your target.
For more information type
help searchinside msfconsole.
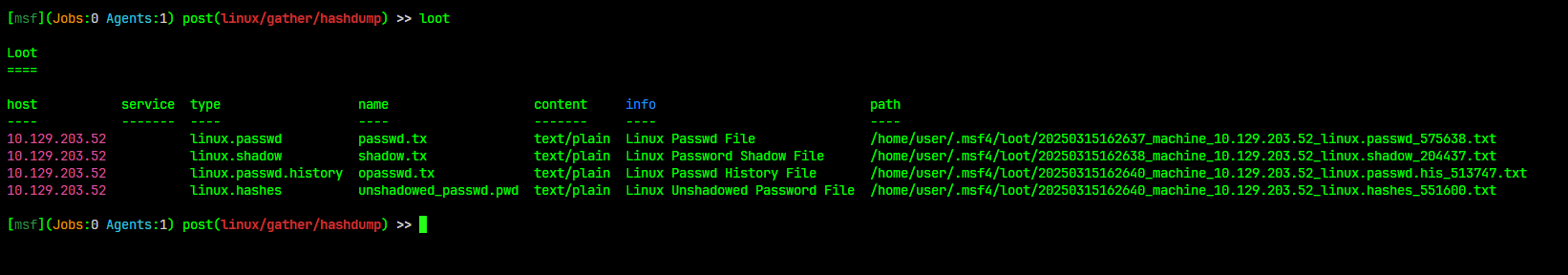
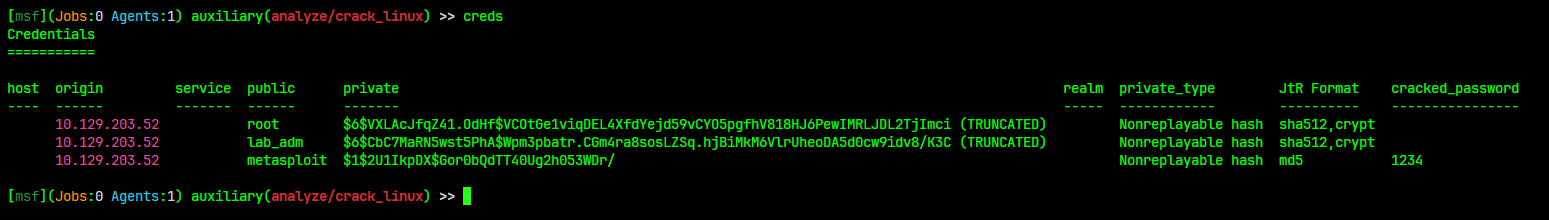
Databases
The Msfconsole has built-in support for the PostgreSQL database system. It is used to track results during complex machine assessments that generate a large amount of data.
For more information type
help databaseinside msfconsole.
-
Start and Initialize database:
# Start PostgreSQL sudo systemctl start postgresql # Initialize database sudo msfdb init -
Workspaces:
# List workspaces msf > workspace -l # Switch workspace msf > workspace <name> # Added workspace msf > workspace -a <name> # Delete workspace msf > workspace -d <name> -
Import Results:
# Import result msf > db_import filename.xml -
Export Results:
# Export result msf > db_export -f xml filename.xml
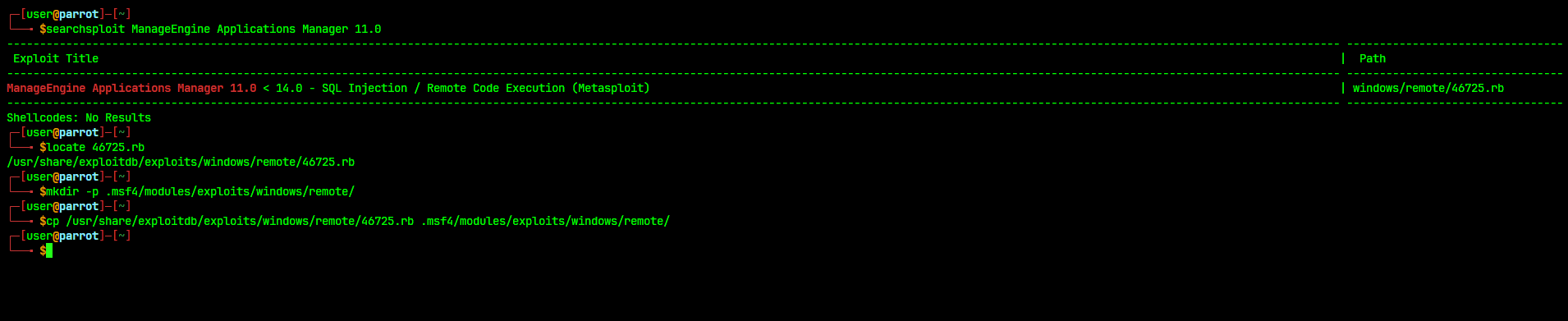
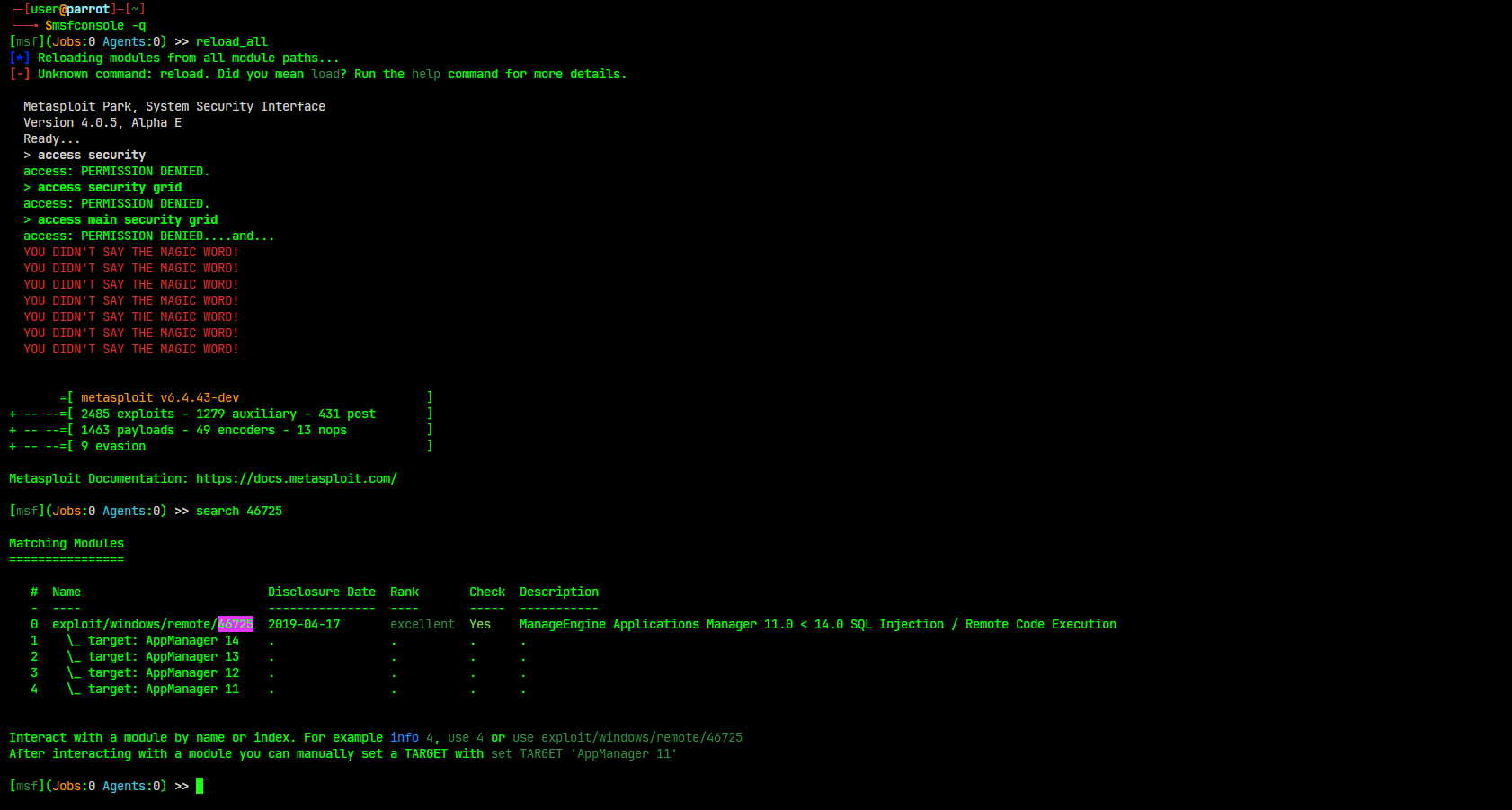
Import exploit from ExploitDB
Sometimes, not all exploits are available in Metasploit. This could mean that Metasploit is not up to date or that the exploit is not included in the official release.
However, the specific exploit we are looking for might be available in ExploitDB as a Metasploit module, which we can import into Metasploit.